Their purpose is to ensure that models operate within safe, legal, and appropriate boundaries for production environments. In real-world scenarios —especially in companies handling sensitive data, regulated processes, or critical information— guardrails are essential to prevent risks such as:
- Unintentional exposure of personal or confidential data.
- Generation of harmful, toxic, or inappropriate content.
- Model manipulation through jailbreak attempts.
- Out-of-context responses or deviations from business objectives.
- Unsafe instructions that could trigger tools or processes incorrectly.
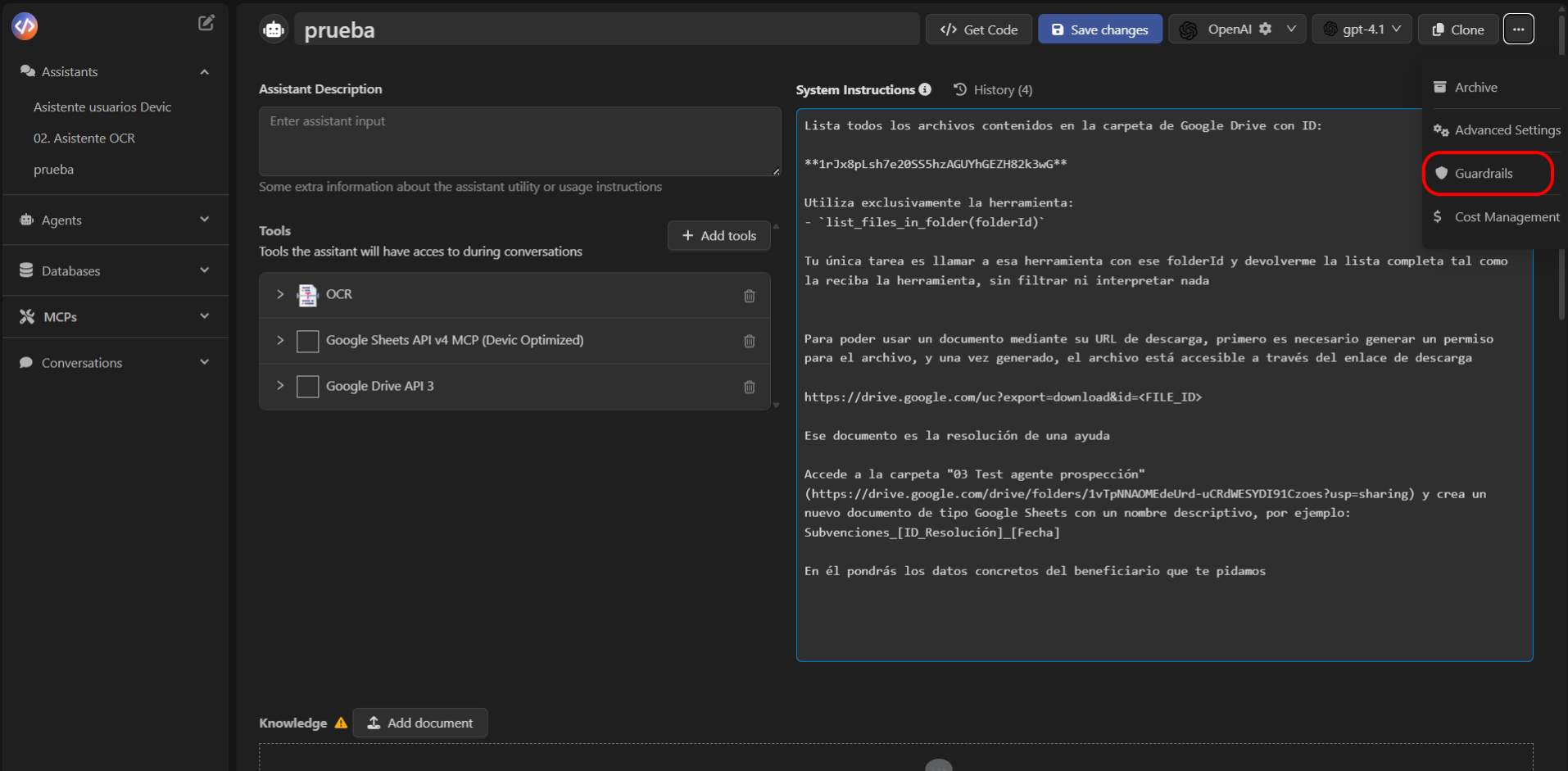
How to Access Guardrails
To configure an assistant’s guardrails:- Open the assistant from the Devic sidebar.
- Select the options menu (⋮) in the top-right corner.
- Click Guardrails.
- Press Add guardrail to create a new one.
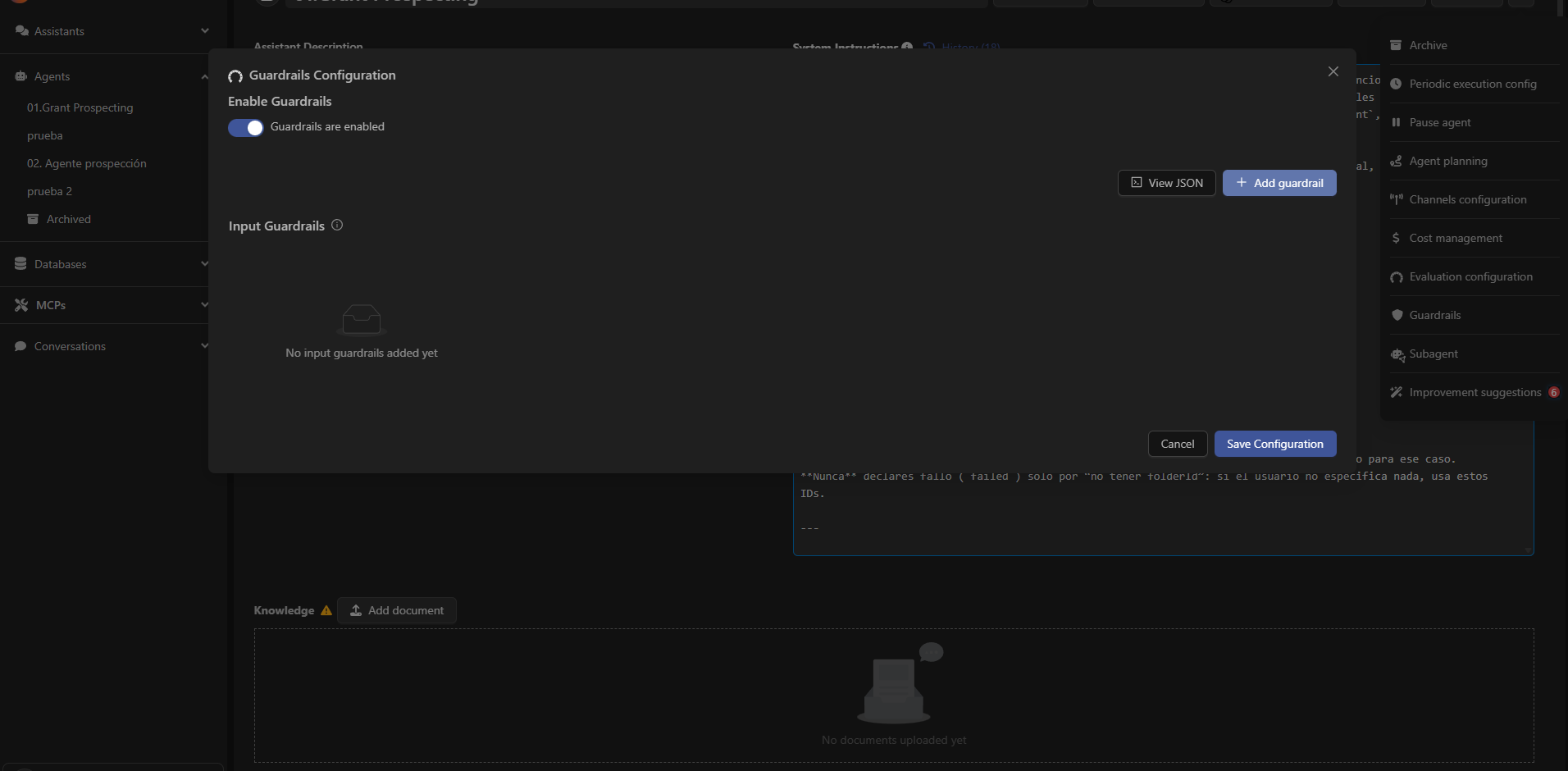
Types of Available Guardrails
Devic currently offers five main categories of guardrails:| Guardrail | Purpose |
|---|---|
| Mask PII | Detects and hides personally identifiable information before it reaches the model. |
| Moderation | Blocks sensitive, toxic, or prohibited content using moderation classifiers. |
| Jailbreak | Detects and prevents attempts to break the model’s safety boundaries. |
| Off Topic Prompts | Prevents the assistant from responding to topics outside the defined scope. |
| Custom Prompt Check | Allows creating personalized rules in natural language to validate or reject instructions. |
Next: Mask PII
Discover how to protect personal and sensitive data using the automatic masking guardrail.